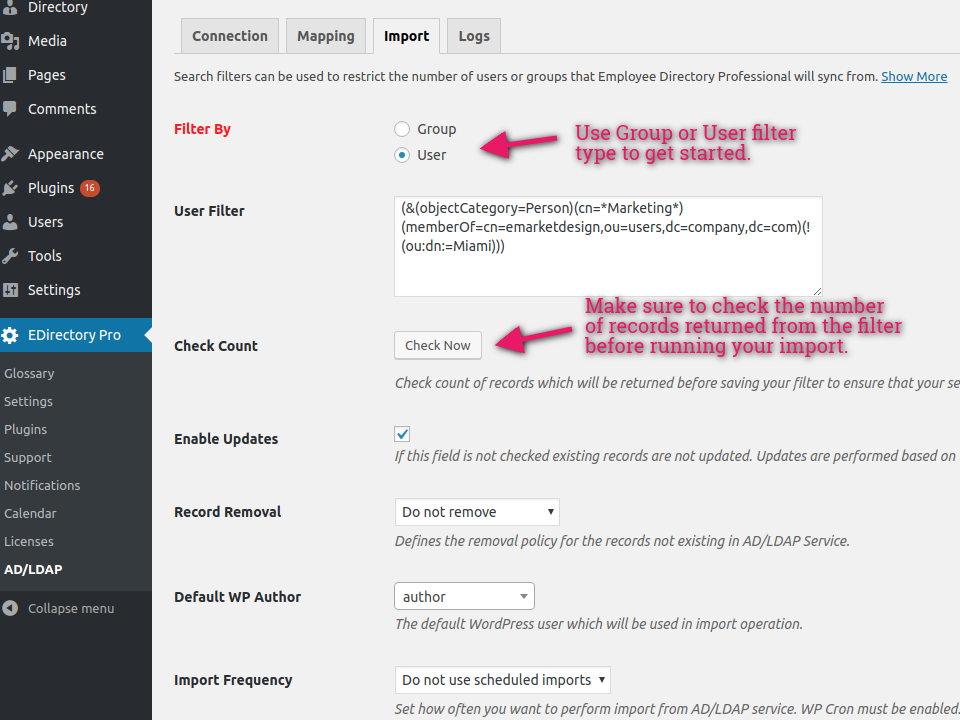
eMD Microsoft Active Directory/LDAP addon is used to integrate our WordPress plugins to LDAP based data stores. eMD Active Directory/LDAP addon allows using LDAP search filters when syncing from Microsoft Active Directory or LDAP servers.
LDAP search filters may be composed of one to many search filter components. You can define search filters under Import tab of the plugin settings. To be able to use LDAP search filters, you must be using at least v2.0 of eMD Microsoft Active Directory/LDAP addon.
Search filters can be used to limit the number of records received from the connected eMD Microsoft Active Directory/LDAP source. Large organizations with many departments or parent child type of multi company structures may have thousands of groups and even more users. Instead of using the default filter which gets all the available records, using a more specific LDAP search filter, you can only get the records that are relevant to your project.
In addition to a text area which is used to define your search filter, a test count button is included to help you check the number of records returned using your search filter.
Using eMD Microsoft Active Directory/LDAP addon, you can construct user or group based search filters. To get started pick a search filter type based on how your organization is configured in your Microsoft Active Directory or LDAP server. The syntax or algorithms that is used in LDAP search filters may change based on the vendor so make sure you check the documentation available before constructing filters.
LDAP terminology defines groups as a collection of users sharing a common attribute. Groups can include actual human users as well as computers, applications or system users. Group filters can help you set the scope of the search to human users.
Group filters are used to limit the search to certain groups or to select groups that include actual users. Based on the results, eMD Microsoft Active Directory/LDAP addon populates the Group Names dropdown where you can additionally narrow down your search scope.
For example, the following search filter limits the groups to be returned to the users in object category of groups and the ones belonging to only to the directory user or directory managers.
(&(objectCategory=Group)(|(cn=directory-users)(cn=directory-managers)))
Please note the usage of & symbol is to express AND operator and the usage of | symbol is to express OR operator. AND operator means all specified filters must be true to return a record. OR operator means at least one specified filter must be true for a record to be returned. Usage of parenthesis helps specify the order of the evaluation for all expressions; evaluate innermost to outermost parenthetical expressions first and evaluate from left to right in any case.
User filters are used to restrict the scope of your LDAP search to certain users sharing a common attribute.
For example, the following filter returns all records matching users belonging to emarketdesign company and tagged with a word containing Marketing but not located in Miami.
(&(objectCategory=Person)(cn=*Marketing*)(memberOf=cn=emarketdesign,ou=users,dc=company,dc=com)(!(ou:dn:=Miami)))
Please note that the usage of * wildcard symbol to filter any word. We also used NOT operator to exclude the users located in Miami from our search. NOT operator is expressed with ! symbol and additional parentheses.
You can also use user LDAP search filters for testing purposes. For example, before running a full initial sync, you can pull your own or team data to make sure the structure is correct and the filter works as expected.
For example, the following filter returns users in eMarket Design working in Marketing department and have Dara Duman or Safiye Duman as their managers.
(&(ou=Marketing)(|(manager=cn=Safiye Duman,ou=Marketing,dc=emarketdesign,dc=com) (manager=cn=Dara Duman,ou=Marketing,dc=emarketdesign,dc=com)))
Search operators are used to narrow the focus of the search. We used some of the search operators in the examples above. The following is a list of all search operators available in LDAP searches:
If a search expression contains an asterisk, left parenthesis, right parenthesis, backslash, or NULL character, it must be escaped to return correct records: